A career in ethical hacking is a dynamic and rewarding path within cybersecurity, offering opportunities to proactively protect digital systems from malicious attacks. This guide, “From Black Hat to White Hat,” is for aspiring professionals, students, and hobbyists, covering the essentials of this field, including key concepts, roles, certifications, and expert insights.
It explains in detail how ethical hacking, also known as white hat hacking, involves the legal and professional practice of simulating cyberattacks on computer systems, networks, or applications. This process is carried out to identify potential security vulnerabilities and weaknesses so that they can be addressed and fixed proactively before malicious hackers have the chance to exploit them.

In direct contrast to black hat hackers, who maliciously exploit computer systems and networks for their own personal gain and often cause significant harm, ethical hackers are individuals who have been explicitly authorized to conduct security testing. Their primary goal is to identify vulnerabilities and weaknesses to strengthen and improve the overall defenses of these systems, ensuring they are better protected against potential cyber threats.
As our world becomes increasingly reliant on digital technologies and online systems, the role of an ethical hacker has grown immensely important in addressing and combating the ever-evolving and more complex cyber threats that organizations face daily.
For individuals who have a strong passion for problem-solving, critical thinking, and tackling technical challenges head-on, ethical hacking offers a well-established, mature, and highly viable career path. This profession not only provides the opportunity to make a significant impact on cybersecurity but also comes with high demand in the job market and attractive, competitive salary packages.
Understanding Key Concepts: Black Hat vs White Hat Hackers
The distinction between black hat, white hat, and gray hat hackers is absolutely fundamental to gaining a comprehensive understanding of the ethical hacking landscape, as each specific type of hacker is primarily defined by their underlying intent, the nature of their actions, and the legality surrounding their activities.
This specific classification system plays a crucial role in clearly distinguishing and separating the diverse motivations, goals, and ethical considerations that influence and guide each distinct group within the much broader and varied hacking community as a whole.
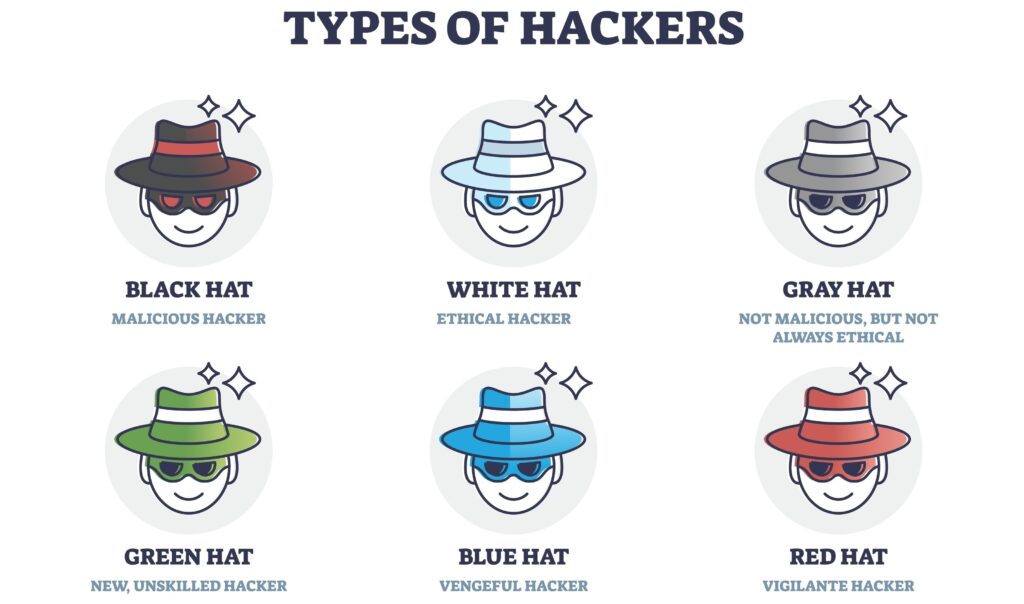
Black Hat Hackers
They are individuals who operate with malicious intent and without any form of authorization or permission. They illegally break into computer systems and networks to steal sensitive data, disrupt services, commit various types of fraud, or cause significant harm to organizations or individuals. These hackers are often motivated by personal financial gain, revenge against a target, or ideological reasons such as promoting a political agenda.
They actively seek out and exploit vulnerabilities in software, hardware, or network configurations to achieve their criminal objectives. Their activities are strictly illegal and are frequently subject to investigation and prosecution by law enforcement authorities worldwide.
White Hat Hackers
They are also known as ethical hackers, operate strictly within legal boundaries, and always with proper authorization to enhance security measures. They conduct thorough penetration testing, detailed vulnerability assessments, and realistic incident simulations to identify potential weaknesses before malicious black hat hackers can take advantage of them.
Their primary objective is to safeguard sensitive data and bolster the cybersecurity defenses of organizations. White hat hackers responsibly disclose any discovered vulnerabilities and adhere strictly to established ethical guidelines and professional standards.
Gray Hat Hackers
They occupy a unique and often misunderstood middle ground in the world of cybersecurity. These hackers may engage in hacking activities without having explicit permission from the target, yet they typically do so without any malicious intent or desire to cause harm.
Gray hats frequently focus on discovering security vulnerabilities and weaknesses within systems, and they might report their findings to the affected organizations—sometimes even requesting a fee or reward for their efforts. However, because their actions are carried out without formal authorization, they can often cross legal boundaries or violate ethical standards.
This ambiguous position highlights the complex relationship between black hat and white hat hackers, with some gray hats occasionally shifting their approach and evolving from one category to another over time.
In Summary
The “From Black Hat to White Hat” narrative vividly captures the transformative journey that many individuals undertake as they redirect their hacking skills from unauthorized, malicious activities toward ethical and fully legal roles within the cybersecurity field.
By deeply understanding these important distinctions between different types of hackers, one can better appreciate the legitimacy and necessity of ethical hacking practices. This narrative also emphasizes the crucial and often underappreciated role that white hat hackers play in actively defending and protecting digital systems, networks, and sensitive information from potential cyber threats and attacks.
Top Careers in Ethical Hacking
Top careers in ethical hacking present a wide array of specialized roles that play a crucial part in safeguarding organizations from increasingly sophisticated cyber threats. Each position emphasizes different facets of cybersecurity, covering everything from proactive offensive testing to comprehensive strategic security planning and implementation.
The following is a detailed overview of some of the most prominent and in-demand career titles, along with their essential responsibilities, all aligned with the latest cybersecurity industry standards projected for 2025:
| Job Title | Description | Key Responsibilities |
|---|---|---|
| Penetration Tester | Also called “pen testers,” these professionals simulate cyberattacks to find security weaknesses before malicious hackers do. | Conduct authorized penetration tests on networks, applications, and systems; use tools like Metasploit and Burp Suite to exploit vulnerabilities; report findings and recommend remediation measures |
| Vulnerability Assessor | Focuses on identifying and analyzing security vulnerabilities in systems and applications. | Perform scans and assessments using automated tools such as Nessus and Qualys; evaluate risk levels; suggest mitigation strategies to reduce exposure points |
| Security Analyst | Monitors, analyzes, and defends against cyber threats in an ongoing capacity. | Monitor network traffic and security alerts for suspicious behavior; conduct log analysis; implement threat response actions; manage security information and event management (SIEM) tools |
| Security Consultant | Advises organizations on cybersecurity strategies, compliance, and best practices. | Conduct security audits and risk assessments; develop security policies; assist with regulatory compliance (e.g., GDPR, ISO 27001); recommend technology and process improvements |
| Security Engineer | Designs, implements, and maintains security infrastructure and controls. | Build and manage firewalls, intrusion detection systems, and encryption protocols; develop security architecture; ensure secure network design |
| Information Security Manager | Oversees the security program and team within an organization. | Lead cybersecurity initiatives; manage budgets and resources; handle incident response coordination; ensure compliance with legal and regulatory standards; train and mentor security personnel |
Role Variations and Scope
In the year 2025, the role of ethical hackers, especially those who are Certified Ethical Hackers (CEH), has significantly expanded beyond the traditional scope of merely conducting penetration testing. These professionals now engage in a much wider range of activities that contribute to comprehensive assessments of an organization’s overall security posture.
Their responsibilities include executing sophisticated social engineering simulations designed to identify human vulnerabilities, implementing continuous threat monitoring systems to detect potential risks in real time, and working closely in collaboration with incident response teams to quickly address and mitigate security breaches.
For instance, CEH experts actively participate in highly realistic and complex Red vs. Blue team exercises, which are specifically designed to sharpen and enhance the organization’s defensive capabilities, making them more resilient against evolving cyber threats.
Some organizations distinguish between penetration testers and ethical hackers, underscoring that ethical hacking is a comprehensive approach that encompasses vulnerability management, social engineering, and proactive threat intelligence.
Emerging Roles and Specializations
The ethical hacking career landscape is continuously evolving and expanding, presenting a wide variety of roles in areas such as:
- Red Team Specialists: Focus on simulating real-world cyberattacks to test organizational defenses holistically.
- Bug Bounty Hunters: Freelancers or professionals who discover and report vulnerabilities to companies in exchange for rewards.
- Digital Forensics Investigators: Analyze cyber incidents to identify attack methods and mitigate future risks.
- Cloud Security Engineers: Specialized in securing cloud infrastructures, an area with rapid growth due to cloud adoption.
- Each role requires a unique skill set, but all emphasize proactive identification and mitigation of cybersecurity risks.
This current snapshot provides a comprehensive overview of the rich and varied diversity found within ethical hacking careers, ranging from highly tactical roles that are primarily focused on detailed penetration testing to more strategic leadership positions that involve overseeing and managing broad organizational security efforts.
Each of these roles offers unique opportunities for professional growth, continuous learning, and the chance to make a meaningful and lasting impact in the critical field of defending against ever-evolving cybersecurity threats.
Essential Skills and Certifications
To achieve success in the field of ethical hacking, professionals must develop a strong and well-rounded combination of advanced technical expertise along with essential soft skills such as communication, problem-solving, and critical thinking.
Additionally, their abilities and dedication are further validated through obtaining recognized industry certifications, which demonstrate their proficiency and commitment to maintaining high standards in cybersecurity practices.
Technical Skills
- Networking Protocols & Concepts: Ethical hackers are required to have a thorough understanding of how data moves and is transmitted across different types of networks. This includes an in-depth knowledge of essential protocols such as TCP/IP, DNS, HTTP/S, FTP, SMTP, and others that govern network communications. Additionally, it is important to be familiar with standard network devices like routers, switches, and firewalls, as these play crucial roles in managing and securing network traffic. Proficiency in using advanced packet analysis tools such as Wireshark and tcpdump is absolutely critical for effectively identifying potential security weaknesses and vulnerabilities within the network infrastructure.
- Operating Systems Proficiency: Experts in the cybersecurity field predominantly work with Unix-based systems such as Linux because these platforms are widely recognized for their robustness and prevalence in security environments. However, possessing a strong understanding of Windows and macOS operating systems is equally crucial, as these platforms are commonly used in various organizational setups. Essential skills include efficiently navigating complex file systems, scripting and automation using tools like Bash or PowerShell, managing running processes and system services, and having a thorough understanding of permissions, user roles, and configurations within Active Directory and similar directory services.
- Programming/Scripting Languages: Proficiency in a wide range of programming languages, such as Python, C, C++, Java, SQL, PHP, and JavaScript, is essential for hackers, as it enables them to write highly customized scripts tailored specifically for exploiting various system vulnerabilities and automating repetitive or complex tasks efficiently. Having a strong foundation and deep coding knowledge is absolutely fundamental not only for understanding the intricate details of different exploits but also for developing effective patches and security measures to protect systems against potential attacks and breaches.
- Penetration Testing Tools & Methods: Having a strong familiarity with widely used tools such as Metasploit, Burp Suite, Nessus, Qualys, and various Kali Linux distributions is essential for effective penetration testing. Ethical hackers utilize both manual techniques and automated testing processes to thoroughly identify potential entry points and security weaknesses within a system. After the vulnerabilities are discovered, these professionals provide detailed recommendations and strategies for mitigation to enhance the overall security posture and protect against unauthorized access.
- Security Frameworks, Cryptography & Encryption: Having a comprehensive understanding of various security standards, cryptographic protocols such as SSL/TLS, AES, and RSA, as well as different encryption methods and certificate management processes, is essential. This knowledge enables ethical hackers to thoroughly assess the security of communications and data protection mechanisms, ensuring robust defense against potential vulnerabilities and cyber threats.
- Social Engineering & Malware Analysis: Effectively recognizing various attack vectors, including sophisticated phishing schemes and impersonation tactics, along with thoroughly analyzing the behavior of malware and the scripts used, completes a hacker’s comprehensive and holistic understanding of potential security threats. This combined knowledge is essential for anticipating and mitigating risks in the cybersecurity landscape.
Soft Skills
- Problem-Solving and Analytical Thinking: Ethical hackers approach challenges by thinking like adversaries, employing creative and strategic analysis of systems to thoroughly anticipate a wide range of potential exploits and vulnerabilities. They use their analytical skills to dissect complex systems, identifying weaknesses before malicious actors can exploit them.
- Ethical Judgment and Integrity: Maintaining exceptionally high ethical standards and demonstrating strong discipline to conduct only authorized testing procedures are essential and non-negotiable requirements. Any history of illegal activity or unethical behavior in the past can and will disqualify candidates from consideration.
- Communication: Possessing the ability to clearly and effectively document findings, thoroughly explain complex technical risks to various stakeholders, and skillfully conduct training or awareness sessions is highly valued and essential in this role. This competency ensures that information is conveyed accurately and understood by all parties involved.
- Continuous Learning: Cybersecurity is a constantly evolving field that changes rapidly; therefore, staying consistently updated with the latest emerging threats, innovative tools, and cutting-edge research is absolutely critical for achieving long-term success and maintaining a strong defense.
Key Certifications to elevate credibility and marketability
Certifications significantly enhance an individual’s credibility within their professional field, opening up a wide array of new and exciting career opportunities. They often serve as a key factor in advancing to higher-level roles and responsibilities.
Additionally, obtaining certifications is frequently associated with the potential for better salaries and improved compensation packages, reflecting the added value and expertise that certified professionals bring to their organizations.
- Certified Ethical Hacker (CEH): Provided by the EC-Council, the Certified Ethical Hacker (CEH) certification validates a professional’s comprehensive knowledge of ethical hacking techniques as well as the relevant legal and regulatory frameworks. This certification is recognized worldwide and is highly regarded within the cybersecurity industry. It emphasizes practical skills related to various hacking tools, methodologies, and security assessment techniques, ensuring that candidates are well-prepared to identify and address potential vulnerabilities in information systems effectively.
- Offensive Security Certified Professional (OSCP): Renowned for its extremely challenging and demanding hands-on practical examination, the OSCP certification demonstrates a profound level of penetration testing expertise. It validates the candidate’s ability to identify vulnerabilities and exploit real-world computer systems in a secure and controlled manner, showcasing practical skills that go beyond theoretical knowledge.
- CompTIA PenTest+: This certification is designed for professionals at the entry to mid-level stages of their careers and provides comprehensive coverage of penetration testing processes. It also includes in-depth knowledge of vulnerability assessment techniques and the essential skills required for effective reporting. This credential prepares individuals to identify, exploit, report, and manage security risks in various environments.
- Certified Information Systems Security Professional (CISSP): This is an advanced and highly respected certification designed specifically for experienced security professionals who have a strong background in the field. It emphasizes a comprehensive understanding of security architecture, management strategies, and regulatory compliance requirements, preparing individuals to handle complex security challenges across various industries.
- GIAC Penetration Tester (GPEN) and Certified Network Defense Architect (CNDA): These are specialized and highly regarded credentials that place a strong emphasis on mastering advanced penetration testing methodologies as well as comprehensive network defense strategies and techniques. They validate expertise in identifying vulnerabilities and implementing robust security measures.
Mastering the right technical skills and obtaining industry-respected certifications are essential for anyone looking to establish a credible and successful career in ethical hacking. Developing a deep understanding of these technical abilities not only builds confidence but also demonstrates expertise to potential employers and clients.
Additionally, maintaining strong ethical foundations and fostering effective communication skills are crucial elements that ensure practitioners consistently act responsibly. These qualities enable ethical hackers to collaborate effectively with organizations, helping them to identify vulnerabilities and improve their overall security posture on a continuous basis.
This comprehensive information has been carefully compiled from the most recent cybersecurity training resources as well as expert career guides, aiming to provide a detailed and cutting-edge perspective on what it truly takes to excel and succeed as a highly skilled ethical hacker in the rapidly evolving landscape of 2025.
Career Roadmap: How to Become an Ethical Hacker
For individuals who are aspiring to enter the ever-evolving and dynamic field of cybersecurity, it is absolutely essential to establish a well-structured and solid career roadmap. This roadmap serves as a crucial guide that helps navigate the complexities of the industry and sets a clear path toward professional success. In this guide, we will provide a detailed, clear, and step-by-step approach on how to become a proficient ethical hacker.
This comprehensive guide covers everything from building your foundational technical skills, understanding key cybersecurity concepts to earning important and widely recognized certifications. Additionally, it emphasizes the significance of gaining practical, hands-on experience through real-world applications.
By diligently following this thoughtfully designed roadmap, you can systematically and effectively develop the deep expertise and practical knowledge needed to thrive and succeed in this high-demand, fast-paced, and rewarding profession.
Acquire Foundational Knowledge
Begin by developing a solid and comprehensive understanding of fundamental IT concepts, including essential networking protocols such as TCP/IP, DNS, and HTTP, which form the backbone of internet communication.
Additionally, gain familiarity with various operating systems like Linux and Windows, as these platforms are widely used in different IT environments. It is also important to learn programming basics, with Python being a particularly popular and versatile language that can help you automate tasks and solve problems efficiently.
Starting your career with entry-level IT positions, such as a technician or network administrator, offers valuable hands-on experience that will allow you to apply theoretical knowledge in real-world situations and steadily build your expertise over time.
Develop Ethical Hacking Skills
Learn the fundamental principles of cybersecurity and ethically exploit various vulnerabilities to enhance your understanding. Utilize a combination of online courses, comprehensive books, and interactive hands-on labs to gain mastery over different attack techniques, defense strategies, and essential security tools such as Metasploit and Wireshark.
Engaging regularly in Capture the Flag (CTF) competitions and participating in diverse hacking challenges further develops your practical skills, allowing you to apply theoretical knowledge in real-world scenarios effectively.
Earn Certifications
Obtain industry-recognized certifications to effectively validate and demonstrate your professional know-how and expertise in the cybersecurity field. Begin your certification journey with the Certified Ethical Hacker (CEH) credential, which offers comprehensive foundational knowledge and essential skills for ethical hacking.
After gaining a solid base, consider advancing to the Offensive Security Certified Professional (OSCP) certification, which is widely respected for its challenging and rigorous hands-on exam that thoroughly assesses your practical penetration testing capabilities in real-world scenarios.
Additionally, there are other highly valuable certifications to pursue that can further enhance your qualifications and career prospects, such as the Certified Information Systems Security Professional (CISSP) and CompTIA Security+, both of which are well-regarded within the industry for their broad coverage of security principles and best practices.
Gain Practical Experience
Actively seek out internships, participate regularly in bug bounty programs, or take on freelance projects to effectively apply and sharpen your skills in real-world environments. Building a comprehensive portfolio that includes well-documented exploits, detailed vulnerability reports, and notable Capture The Flag (CTF) competition achievements significantly enhances your credibility and greatly improves your chances during job applications and interviews.
This hands-on practical experience not only clearly demonstrates your technical skills and abilities but also highlights your strong commitment and genuine passion for the field you are dedicated to.
Apply for Entry-Level Positions
Begin your professional career by taking on entry-level positions such as a junior penetration tester, vulnerability assessor, or security analyst. These foundational roles offer invaluable hands-on experience with a variety of security tools and technologies, while also fostering effective collaboration within security teams.
Gaining practical knowledge and hands-on experience while working alongside highly skilled and experienced professionals in these positions will thoroughly prepare you for more advanced, specialized, and challenging roles in the cybersecurity field. This invaluable exposure will help you develop a deeper understanding of complex security concepts and industry best practices.
Continuous Learning and Specialization
Cybersecurity is an incredibly fast-evolving and dynamic field that requires constant vigilance and a commitment to regularly updating your knowledge. It is essential to stay informed about the latest cyber threats, emerging hacking techniques, and continuous advancements in security frameworks and technologies.
To build a strong expertise, consider specializing in specific areas such as cloud security, which focuses on protecting data and applications in cloud environments, red teaming, which involves simulating cyberattacks to test defenses, or incident response, which deals with managing and mitigating security breaches effectively.
As you gain more experience and develop your skills, pursuing leadership roles, compliance management, or consulting opportunities becomes a natural and rewarding progression in your cybersecurity career path.
In Summary
This detailed career roadmap clearly highlights that ethical hacking is not a sprint but rather a marathon, demanding consistent and ongoing learning, strict ethical discipline, and extensive hands-on practical experience.
A deep passion for cybersecurity combined with a strong commitment to protecting valuable digital assets will be the key drivers that fuel long-term success and growth in this challenging yet rewarding field.
Benefits of a Career in Ethical Hacking
A career in ethical hacking provides a wide range of significant benefits, making it an exceptionally attractive and highly sustainable profession in the rapidly evolving, technology-driven world we live in today.
This field continues to grow in importance as organizations increasingly rely on digital systems and cybersecurity to protect sensitive information. Here’s a comprehensive and detailed overview, supported by the most recent data and industry insights projected for the year 2025:
- High Demand and Job Security: With the explosive growth of cybersecurity threats worldwide, organizations across sectors continuously seek skilled ethical hackers to protect their systems. This demand is global and projected to remain robust, ensuring excellent job stability and multiple opportunities in various industries, including finance, healthcare, government, and technology.
- Competitive Salaries: Ethical hacking is a well-compensated field. Entry-level ethical hackers in the US earn between approximately $89,000 and $112,000 annually, with experienced professionals averaging $147,000 or more depending on their skills, certifications, and location. Salaries vary globally; for instance, in Nigeria, Certified Ethical Hackers earn an average of around ₦3,360,000 (~$7,000) annually, with pay increasing as expertise grows.
- Continuous Learning: Cybersecurity is a rapidly evolving field with new vulnerabilities and hacking techniques constantly emerging. Ethical hackers must stay updated on the latest technologies, threats, and defense mechanisms, which makes the work intellectually stimulating and engaging. This continuous learning environment is ideal for those passionate about technology and problem-solving.
- Meaningful Impact: Ethical hackers play a vital role in safeguarding sensitive information, critical infrastructure, and personal data against cybercriminals. Their work helps prevent identity theft, financial fraud, privacy breaches, and even threats to national security. This sense of purpose and contribution to a safer digital world is a significant motivational factor for many in the field.
- Career Growth Opportunities: The ethical hacking profession offers diverse pathways for advancement. Professionals can progress into senior technical roles such as senior penetration tester or security architect, branch into cybersecurity consulting, or move into managerial positions like Information Security Manager or Chief Information Security Officer (CISO). Specializations in cloud security, threat intelligence, or incident response provide further growth options.
In Summary
Ethical hacking is not only a financially rewarding career but also one that provides strong job security, continuous intellectual challenges, and the chance to make a significant impact in the field of cybersecurity.
These combined factors create a highly attractive and fulfilling career path for both aspiring IT professionals who are just starting and those looking to make a career change. The dynamic nature of cybersecurity ensures that ethical hackers are always learning and evolving, making it a stimulating and worthwhile profession for anyone interested in technology and security.
Current Trends and Developments in Ethical Hacking
Current trends and developments in ethical hacking for the year 2025 underscore a rapidly evolving and dynamic field that is significantly influenced by continuous technological advancements, emerging new work models, and shifting government priorities.
The landscape of ethical hacking is expanding and adapting at an unprecedented pace, driven by innovations in technology and the increasing complexity of cyber threats. Below is a comprehensive overview of the most important trends that are currently shaping and will continue to shape the profession in the near future:
Bug Bounty Programs
Bug bounty platforms have become mainstream in cybersecurity, enabling organizations to crowdsource security testing by inviting ethical hackers to find and report vulnerabilities. These programs gamify ethical hacking and reward participants financially for valid discoveries, creating incentives for continuous security improvement.
Leading platforms such as Intigriti, Bugcrowd, Synack, and HackerOne host programs spanning industries including finance, tech, and government. Bug bounty involvement also helps ethical hackers sharpen skills and build reputations in a legal and structured environment.
AI and Automation
Artificial intelligence (AI) and machine learning tools are revolutionizing ethical hacking and cybersecurity. AI-powered systems automate threat detection by analyzing massive data sets for behavioral anomalies in real time.
These tools accelerate vulnerability assessments, reduce manual labor, and enhance incident response by prioritizing risks and mitigating threats before human analysts intervene. Ethical hackers increasingly leverage AI-enabled technologies for penetration testing, malware analysis, and threat intelligence. Automation supports more proactive and scalable security defense strategies.
Remote and Freelance Opportunities
The cybersecurity workforce is embracing remote and freelance work models, broadened by global digital connectivity and demand for flexible expertise. Ethical hackers can work remotely on contracts, participate in bug bounty programs, or freelance as consultants, expanding their access to global job markets beyond traditional office settings.
Platforms that specialize in remote cybersecurity jobs, along with a wide range of remote collaboration tools, have now become essential and standard components in the industry. These technologies enable seamless access and participation for talented professionals located in diverse geographic regions, including those in emerging markets that previously had limited opportunities.
This widespread availability plays a crucial role in connecting highly skilled individuals with employers from all around the world, thereby fostering the development of a more inclusive, diverse, and significantly expansive cybersecurity workforce that can meet the growing demands of the industry.
Government Initiatives
Governments worldwide are intensifying cybersecurity efforts by updating regulations, increasing budgets, and integrating ethical hackers into national defense strategies. Public-private partnerships encourage collaboration for threat intelligence sharing and joint incident response.
Initiatives such as modernizing critical infrastructure cybersecurity (energy grids, water systems), strengthening endpoint detection, Zero Trust frameworks, and enhancing phishing-resistant authentication protocols are being prioritized.
Governments around the world actively seek skilled ethical hackers to rigorously test their cybersecurity defenses, participate in comprehensive Red Teaming exercises, and help secure critical national assets from potential cyber threats.
This growing demand creates a wide range of promising career opportunities within the public sector cybersecurity field, offering professionals the chance to contribute to national security and protect important government infrastructure.
In Summary
These developments clearly signify that the field of ethical hacking is becoming increasingly sophisticated and advanced, deeply integrated with a wide range of emerging and cutting-edge technologies. Additionally, ethical hacking is becoming more accessible through the adoption of flexible and adaptive work models that allow professionals to operate efficiently in diverse environments.
Staying up-to-date and current with these rapidly evolving trends and innovations is absolutely essential for ethical hackers who aim to maintain their relevance, enhance their skills, and maximize their overall impact within the constantly changing cybersecurity ecosystem.
FAQs
What is the difference between an ethical hacker and a black hat hacker?
Ethical hackers work with legal permission to identify and fix security weaknesses to protect systems. Black hat hackers exploit systems illegally for malicious purposes such as stealing data or causing harm. The key difference lies in intent, authorization, legality, and outcome.
Do I need a computer science degree to become an ethical hacker?
While obtaining a degree can certainly be beneficial and provide a strong foundation, it is not always mandatory or required. Many employers place a higher priority on specific certifications such as CEH (Certified Ethical Hacker) and OSCP (Offensive Security Certified Professional), as well as practical skills and extensive hands-on experience. These qualifications often carry more weight in the hiring process than formal academic education alone.
How long does it take to become a certified ethical hacker?
Becoming certified generally takes anywhere from a few months up to a full year, depending largely on an individual’s prior background, the amount of time and effort they dedicate to studying, and how thoroughly they prepare for the certification exams. The timeline can vary significantly based on these factors.
Are ethical hackers in demand globally?
The rapidly increasing prevalence of cyber threats around the world is driving a significantly high demand for skilled ethical hackers across a wide range of sectors, including private companies, government agencies, and specialized cybersecurity firms on a global scale. This growing need highlights the critical role ethical hackers play in protecting sensitive information and maintaining digital security in today’s interconnected environment.
What are some key certifications for ethical hackers?
Among the most highly respected and sought-after certifications in the cybersecurity field are the Certified Ethical Hacker (CEH) and the Offensive Security Certified Professional (OSCP). These credentials are widely recognized for their rigorous standards and practical focus on ethical hacking and penetration testing.
Additionally, there are other valuable certifications that professionals should consider when aiming to advance their careers, such as CompTIA Security+, which provides a solid foundation in security principles, PenTest+, which focuses specifically on penetration testing skills, and the Certified Information Systems Security Professional (CISSP), which is tailored for those pursuing more advanced and managerial roles within the cybersecurity domain.
In Conclusion
Ethical hacking presents a compelling career path for aspiring IT professionals, students, and hobbyists keen on cybersecurity. It offers high demand, lucrative salaries, continuous intellectual growth, and meaningful work defending valuable digital assets.
Understanding the differences among the different types of hackers and fully embracing the essential principles of ethical hacking enables individuals to transform their natural curiosity into a powerful and positive force—effectively moving their skills and mindset “From Black Hat to White Hat.”
With the right skills, certifications, and hands-on experience, one can embark on an exciting journey through numerous specialized roles, contributing to a safer digital world while advancing professionally. Aspiring ethical hackers should seize opportunities for learning, certifications, and practical exposure to build a strong foundation and thrive in this essential and dynamic career.
Discover more from SkillDential
Subscribe to get the latest posts sent to your email.


