Cloudflare is widely recognized as a leading content delivery network (CDN) and a top provider of internet security services, trusted by millions of users and organizations around the world to ensure websites remain fast, secure, and consistently available.
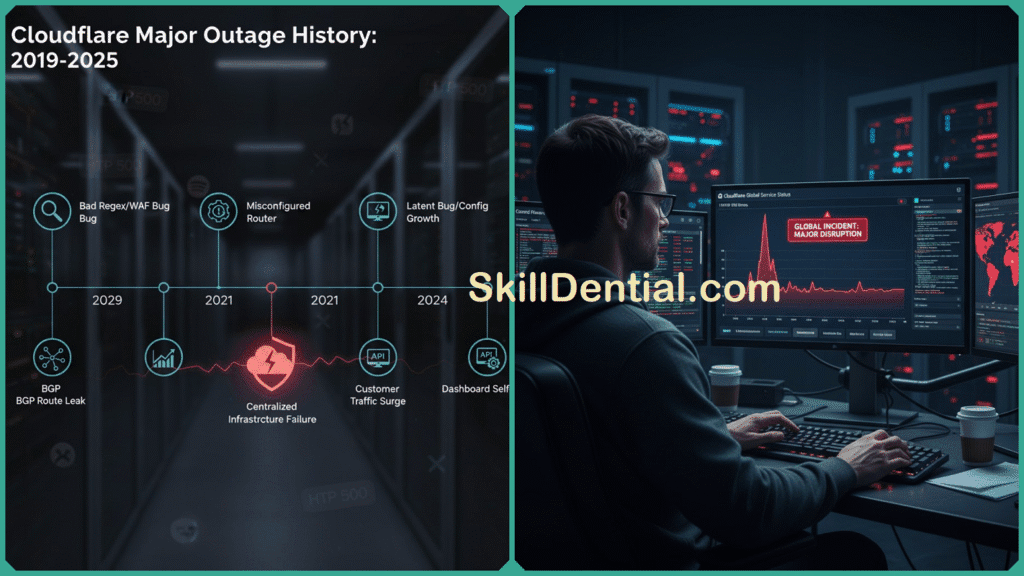
Despite its strong reputation for reliability and performance, Cloudflare has encountered several significant outages spanning the years from 2019 through 2025. These notable incidents provide a valuable and unique insight into the intricate complexities and inherent vulnerabilities present within today’s advanced internet infrastructure.
For Site Reliability Engineers (SREs), Chief Technology Officers (CTOs), security architects, analysts, and technical journalists, having a comprehensive and detailed understanding of the history behind these Cloudflare downtimes is essential.
This post thoroughly examines the root causes, recurring systemic failure patterns, and key lessons learned from the most significant and impactful Cloudflare downtimes that have occurred over this period. By providing a definitive, well-researched, and data-backed record, this analysis aims to support professionals in developing more effective resilience strategies and improving infrastructure risk management practices across their organizations.
Key Concepts and Frameworks
Cloudflare is a comprehensive internet infrastructure services provider primarily offering Content Delivery Network (CDN), Domain Name System (DNS) management, and Web Application Firewall (WAF) functionalities to optimize website performance and security.
As a CDN, Cloudflare caches content on servers distributed globally, reducing latency by serving users from locations nearest to them, while the DNS service handles domain name resolutions, directing traffic efficiently and securely. By proxying traffic through its network, Cloudflare protects websites from threats such as distributed denial-of-service (DDoS) attacks and enhances privacy by masking origin IP addresses.
Its WAF service filters incoming web traffic to block malicious requests and prevent attacks like SQL injection or cross-site scripting. Because Cloudflare acts as a centralized backbone for many internet services, a failure in its system can create a Single Point of Failure (SPOF), disrupting access to numerous websites and services globally.
Cloudflare downtimes can arise from a variety of technical failure types, each contributing to service disruptions in different ways:
- Software Bugs: Errors or hidden issues that are introduced during software updates or deployments, which can cause unexpected interruptions or significantly degrade the quality of service. These bugs may remain unnoticed initially, but can lead to serious problems affecting the overall functionality and user experience of the software.
- Configuration Errors: Mistakes that occur during mass configuration changes, such as incorrectly setting routing tokens or misconfiguring firewall rules, can lead to cascading failures and disrupt a wide range of services simultaneously. These errors often result from oversight or a lack of thorough testing and can have significant impacts on network stability and service availability.
- BGP Route Leaks occur when there are network routing misconfigurations that cause internet traffic to be incorrectly directed or unintentionally dropped, leading to significant disruptions in connectivity. These misconfigurations can result in data packets taking inefficient or unintended paths across the network, severely impacting the overall performance and reliability of internet services. Such leaks often arise from errors in routing policies or improper route announcements between autonomous systems, which can cause widespread connectivity issues for users and organizations relying on stable network communication.
- WAF Bugs: Situations in which security filtering software inadvertently blocks legitimate and trusted traffic, causing the very protection mechanisms designed to safeguard systems to instead become sources of service disruptions and failures. These issues can lead to unintended denial of access for genuine users, effectively transforming security measures into obstacles that hinder normal operations and user experience.
- Credential Rotation Failures: Issues encountered during the automatic updating or rotation processes of authentication credentials that result in components being unable to connect or authorize correctly. These failures can disrupt system functionality by preventing seamless communication and access between different parts of the infrastructure, leading to potential downtime or security risks if not promptly addressed.
- Control Plane Failures: These are failures that occur specifically in management interfaces or administrative dashboards. While such failures do not directly impact the actual delivery or flow of data within the network, commonly known as the data plane, they significantly disrupt administrative functions and user control capabilities. This means that although data transmission might continue without interruption, the ability to manage, monitor, or configure the system is impaired, causing challenges in overseeing network operations and performing necessary administrative tasks.
This type of categorization is extremely helpful in gaining a deeper understanding of the various ways in which complex and highly integrated infrastructure components can malfunction or fail. It highlights the fact that internal operational risks, such as configuration errors or software bugs, often play a more significant role in causing widespread Cloudflare disruptions than external attacks or cyber threats.
By concentrating their efforts on identifying and addressing these internal vulnerabilities, organizations can more effectively anticipate a wide range of potential issues. This proactive approach enables them to strengthen their overall resilience, significantly reducing the risk of experiencing large-scale service interruptions. As a result, they are better prepared to maintain continuous operations and safeguard their critical functions in the face of unexpected challenges.
Major Cloudflare Downtimes (2019–2025)
Here is a comprehensive and detailed explanation of the major Cloudflare downtimes that occurred from 2019 to 2025, offering an in-depth look into the technical context behind each incident as well as the significant impact these events had on users and services worldwide:
June 24, 2019: Internet Traffic Jam with Verizon
The outage was triggered by significant traffic congestion issues involving Verizon’s network, which was interconnected with Cloudflare’s infrastructure. This situation caused widespread and prolonged service disruptions across several major and popular websites, including Hulu, Xbox Live, and Feedly, mainly impacting users located in the US and parts of Europe.
The incident underscored the fragility and complexity of dependencies between major internet service providers and content delivery network (CDN) providers, highlighting the considerable risks related to inter-provider traffic management, routing, and capacity limits during peak loads.
July 2019: WAF Bug Incident
Cloudflare’s Web Application Firewall (WAF), which is specifically designed to filter out and block potentially malicious traffic from reaching web applications, introduced a software bug that unintentionally blocked large amounts of legitimate user traffic.
As a result, this caused significant access outages for numerous users across various sites, effectively illustrating how even protective security tools can inadvertently become Single Points of Failure (SPOFs) within a system.
This incident highlighted the critical importance of implementing robust testing procedures and fail-safe mechanisms in security components to prevent the accidental blocking of legitimate user activity and maintain uninterrupted service availability.
November 2, 2023: Control Plane and Analytics Outage
On November 2, 2023, Cloudflare experienced a significant failure in its control plane, the critical system responsible for managing vital administrative tasks such as accessing the dashboard and configuring services. This disruption caused several important services, including:
- Workers KV (Cloudflare’s key-value storage solution)
- Access (which handles identity verification and access management)
- The Cloudflare dashboard itself to become temporarily inaccessible to users
Despite these challenges, the data plane—the component that handles the actual delivery of content to end users—remained mostly stable and continued functioning effectively. This incident underscored the increasing complexity and interdependence of modern layered service architectures, demonstrating how outages in administrative interfaces can still have a profound impact on overall operations and the ability to manage user access efficiently.
March 21, 2025: Credential Rotation Failure in R2 Gateway
An outage lasting more than an hour occurred on a global scale due to errors in the automatic credential rotation processes for the R2 Gateway, which is responsible for managing authorizations for Cloudflare Workers’ object storage backends.
This failure resulted in complete write failures and partial read failures across the entire platform. The incident clearly demonstrated the critical importance of credential and cryptographic management systems in cloud infrastructure and highlighted the significant risks and potential impacts caused by their failure.
November 2025: Internal Service Degradation and WARP Disruption
A significant internal degradation of Cloudflare’s core service infrastructure caused widespread intermittent failures, including:
- Error pages are being displayed
- Stalled login flows are preventing user access
- Broken APIs are disrupting application functionality
As part of the extensive remediation efforts, Cloudflare had to temporarily disable its WARP VPN service, specifically in the London region, to help contain and resolve the issue. This outage underscored the complex operational challenges involved in real-time incident recovery and demonstrated how emergency mitigation measures, while necessary to stabilize the overall network, can sometimes compromise certain user experiences temporarily.
In Summary
Each of these incidents offers incredibly valuable and detailed lessons on the critical importance of continuous monitoring, strategic diversification, and comprehensive resilience planning within centralized internet infrastructure. This is especially crucial for key providers such as Cloudflare, whose services underpin vast portions of the internet.
Together, these events vividly illustrate the intricate technical nuances and the underlying systemic fragility that can arise from seemingly routine activities like configuration changes, software deployments, the management of authentication processes, and the complex interdependence between control and data planes in today’s advanced network services.
These lessons clearly emphasize how even the smallest and seemingly insignificant oversights can quickly cascade into much larger and widespread disruptions, affecting multiple areas and systems. This highlights the critical need for implementing robust safeguards and adopting proactive risk management strategies to prevent such issues from escalating and causing extensive damage.
Systemic Patterns and Insights
Analyzing Cloudflare’s significant outages from 2019 through 2025 reveals several recurring systemic patterns that are crucial for fully understanding the inherent fragility and the operational risks associated with managing large-scale centralized internet infrastructure:
- Configuration and Software Deployment Risks: Most significant outages primarily originated from internal changes, including software updates, configuration modifications, or deployment errors, rather than from external cyberattacks or malicious intrusions. This reality underscores the exceptionally high operational risk associated with managing increasingly complex software and large-scale systems, where even seemingly minor mistakes or oversights can rapidly cascade into widespread, global service disruptions that affect millions of users.
- Growing Complexity and Fragility: Cloudflare’s ongoing and continuous integration of new and diverse services and features, such as the Web Application Firewall (WAF), Workers KV, and the R2 Gateway, has significantly increased the overall complexity of the system. This steady growth in functionality and capabilities inevitably heightens the fragility of the entire infrastructure, as failures occurring in what may seem like auxiliary or peripheral components—such as the control plane or authentication systems—have the potential to impact and disrupt broad service availability. This situation clearly demonstrates that achieving true robustness requires a very careful and deliberate architectural segregation of critical functions to ensure resilience and minimize the risk of widespread outages.
- Vendor Risk Concentration: The historical evidence clearly demonstrates the significant risks involved when organizations rely heavily on a single, large provider such as Cloudflare for critical internet infrastructure services. When too much dependence is placed on one provider, it creates a single point of failure that has the potential to disrupt extensive portions of online traffic and various digital services simultaneously. These real-world incidents and experiences strongly support and reinforce the arguments for IT leaders and decision-makers to seriously consider adopting multi-CDN or multi-cloud strategies. By diversifying their technology providers and infrastructure, organizations can effectively spread out risks, enhance overall system resilience, and reduce the likelihood of widespread outages or disruptions.
- Incident Recovery Challenges: Cloudflare’s mitigation efforts during outages occasionally resulted in temporary feature blackouts or limited user access, such as the disabling of WARP in London during the 2025 incident. These necessary but disruptive measures highlight the complex operational challenge of finding the right balance between quickly recovering from incidents and maintaining uninterrupted service continuity, along with a positive user experience during widespread and large-scale failures. This trade-off underscores the difficult decisions involved in prioritizing rapid incident response while minimizing the impact on end users.
Gaining a thorough understanding of these patterns greatly assists IT directors, site reliability engineers (SREs), and security architects in the crucial task of designing infrastructure that is significantly more resilient and reliable.
This knowledge also plays a vital role in guiding strategic decision-making processes aimed at effectively mitigating the various risks associated with dependencies on centralized services. The analysis underscores the urgent and critical need for implementing robust and well-structured internal change management processes, as well as promoting architectural compartmentalization to isolate and contain potential failures.
Additionally, it underscores the critical importance of diversifying risk by actively engaging and collaborating with multiple vendors. This approach helps to avoid reliance on a single point of failure, thereby significantly enhancing the overall stability and resilience of the entire system in the long term.
Actionable Recommendations for IT Leaders
Here are detailed and actionable recommendations specifically designed for IT leaders and architects, drawing from Cloudflare’s extensive downtime history, aimed at significantly enhancing the overall reliability and resilience of your infrastructure:
- Invest in Vendor Diversification: Avoid depending exclusively on just one CDN or DNS provider, such as Cloudflare. Incorporating multiple vendors into your infrastructure helps spread out the risks by removing single points of failure. This approach allows you to reroute traffic seamlessly and maintain continuous service availability, even when one provider faces an unexpected outage or disruption. By diversifying your vendor portfolio, you enhance the overall resilience and reliability of your network operations.
- Enhance Monitoring & Alerts: Implement a comprehensive and multi-layered monitoring system that thoroughly covers all critical components, including the control plane (management interfaces), the data plane (responsible for actual content delivery), and the authentication and credential management systems. By establishing early detection mechanisms for any anomalies or irregularities across these multiple layers, organizations can effectively preempt potential outages and significantly reduce the time required for incident detection and response, ultimately ensuring higher system reliability and performance.
- Automate Failovers: Implement robust automated failover mechanisms along with dynamic traffic rerouting capabilities within your system architecture. Whenever an outage or failure is detected, the system can instantly redirect traffic to backup servers or alternate service providers, ensuring continuous operation. This approach significantly reduces service interruptions and downtime by eliminating the need for manual intervention during critical failure events.
- Review Security Tool Dependencies: Thoroughly evaluate Web Application Firewalls (WAFs) and other critical security components with a critical eye, recognizing them as potential Single Points of Failure within your infrastructure. It is essential to develop robust compensating controls or well-designed fallback strategies to ensure that security measures do not unintentionally block legitimate user traffic or negatively impact system availability during incidents. Taking these precautions helps maintain a balanced approach between strong security enforcement and uninterrupted service delivery.
- Foster Incident Preparedness: Develop and continuously update comprehensive and detailed incident response playbooks that draw upon the valuable lessons learned from Cloudflare’s previous outages and disruptions. These playbooks should include clear, step-by-step remediation procedures to guide teams through the recovery process efficiently. Additionally, incorporate well-defined communication protocols to ensure timely and effective information sharing during incidents. Clearly outline roles and responsibilities for all stakeholders involved, enabling faster decision-making and coordinated efforts to accelerate recovery times and significantly enhance the overall organizational resilience against future incidents.
Adopting these carefully considered recommendations will empower IT leadership teams to design and build infrastructures that are significantly more robust and flexible, effectively mitigating the various risks highlighted by Cloudflare’s extensive historical outage record.
By implementing this strategic approach, organizations can achieve a well-balanced combination of risk management, cost efficiency, and operational simplicity, all of which are crucial for sustaining consistently high availability.
This becomes particularly crucial in today’s rapidly evolving and increasingly interconnected digital ecosystem, where uninterrupted and reliable service is absolutely vital for maintaining seamless business continuity and preserving strong user trust over time.
FAQs
What causes most Cloudflare outages?
Most major Cloudflare outages are caused by internal software bugs, configuration errors, or failures in credential management systems—issues introduced during updates or operational changes—rather than by direct external cyberattacks. These internal failure modes often cascade to impact large portions of Cloudflare’s network services.
How long do Cloudflare outages typically last?
The duration of Cloudflare outages can range from under an hour to several hours, depending on the complexity of the issue. For example, the March 2025 credential rotation failure caused a roughly 1-hour and 7-minute global outage, while the November 2023 control plane outage lasted nearly two days in limited capacity during partial recovery phases.
Can Cloudflare outages affect all users globally?
Some Cloudflare incidents have had global or multi-region impacts, disrupting access to major websites and online services worldwide. Other outages may be localized or affect only specific Cloudflare services or regions, reflecting the distributed nature of their infrastructure.
How can companies reduce downtime risks while using Cloudflare?
To effectively mitigate the risks associated with downtime, companies should :
- Diversify their CDN/DNS providers to avoid reliance on a single vendor.
- Implement multi-layer monitoring covering data plane, control plane, and authentication subsystems.
- Automate failovers and traffic rerouting to maintain availability during disruptions.
- Assess and mitigate risks posed by security tools like WAFs that might act as single points of failure.
- Develop and regularly update incident response playbooks based on historical outage learnings.
What is a control plane failure, and why does it matter?
The control plane manages Cloudflare’s administrative interfaces, APIs, configuration settings, and analytics services. A failure in this plane disrupts dashboards and user management tools, complicating service configuration and monitoring, even while the data plane (actual content delivery) remains operational. Control plane outages diminish operational visibility and slow incident recovery, impacting customers’ ability to manage their services effectively.
In Conclusion
The history of Cloudflare downtime spanning from 2019 to 2025 reveals not only the intricacies but also the significant challenges involved in maintaining such a vast and centralized internet infrastructure. Despite Cloudflare’s extensive expertise and advanced technology, its outages highlight the inherent risks and vulnerabilities primarily caused by internal configuration changes and system updates rather than external cyber threats or attacks.
For reliability engineers, technical leadership teams, and security architects, these valuable lessons strongly justify the strategic emphasis on vendor diversification, the implementation of layered and comprehensive monitoring systems, and the design of robust failover resilience mechanisms to ensure continuous service availability and mitigate potential points of failure.
Gaining a thorough understanding of these outages in detail enables decision-makers to design and implement more resilient and robust internet infrastructures. This knowledge helps ensure that essential and critical services remain operational and secure, even as the digital landscape becomes increasingly intricate and challenging to navigate.
Discover more from SkillDential
Subscribe to get the latest posts sent to your email.